A wide area network (WAN) is a large network of information that is not tied to a single location. MCQ 29: Which is not the application level protocol? AH is a protocol that provides authentication of either all or part of the contents of a datagram by the addition of a header. A firewall is a network security device that monitors incoming and Selectors can include source and destination address, port numbers if relevant, application IDs, protocols, etc. public key system MCQ 170: _______________ is the mathematical procedure or algorithm which produces a cipher-text for any specified plaintext. cipher scricpt MCQ 143: A substitution cipher replaces one symbol with the ________________. Ideally, any institution would want its own private network for communication to ensure security. 1989 However, if you want a job working on computer networks, youll need to develop your troubleshooting skills to match. https Computer networking is constantly evolving, and what was once considered a network security best practice may soon be a thing of the past. IKE is the automatic key management protocol used for IPsec. Protocol Read more information about OFAC's Sanctions Programs: Russia-related Sanctions Iran Sanctions North Korea Sanctions 49151 to 65535 Application design bugs may bypass security controls This need gave rise to develop a security solution at the IP layer so that all higher-layer protocols could take advantage of it. Agree Outgoing IP datagrams go from the SPD entry to the specific SA, to get encoding parameters.  Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. Select one: A. 3 and 4 None of the above. MCQ 113: How many keys does the Triple DES algorithm use? None of the above, Rivest, Shamir, Adleman MCQ 164: Which of the following is not a vulnerability of the application layer? RAA Algorithm, MCQ 110: Match the following List 1 and List 2 :
Cant Say Origin authentication and data integrity. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Block Cipher. Monoalphabetic Cipher. Although authentication and confidentiality are the primary services provided by ESP, both are optional. True or False? Strong security often involves using multiple approaches, known as layered security or defense in depth to give organizations as many security controls as possible. It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. Technically, key management is not essential for IPsec communication and the keys can be manually managed. cipher text It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). Transposition-based office each day over a virtual private network (VPN). Public key based In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Virtually all computer networks have vulnerabilities that leave them open to outside attacks; further, devices and networks are still vulnerable even if no one is actively threatening or targeting them. None of the above. private None of the above. SPD can be considered as a packet filter where the actions decided upon are the activation of SA processes.
Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. Select one: A. 3 and 4 None of the above. MCQ 113: How many keys does the Triple DES algorithm use? None of the above, Rivest, Shamir, Adleman MCQ 164: Which of the following is not a vulnerability of the application layer? RAA Algorithm, MCQ 110: Match the following List 1 and List 2 :
Cant Say Origin authentication and data integrity. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Block Cipher. Monoalphabetic Cipher. Although authentication and confidentiality are the primary services provided by ESP, both are optional. True or False? Strong security often involves using multiple approaches, known as layered security or defense in depth to give organizations as many security controls as possible. It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. Technically, key management is not essential for IPsec communication and the keys can be manually managed. cipher text It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). Transposition-based office each day over a virtual private network (VPN). Public key based In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Virtually all computer networks have vulnerabilities that leave them open to outside attacks; further, devices and networks are still vulnerable even if no one is actively threatening or targeting them. None of the above. private None of the above. SPD can be considered as a packet filter where the actions decided upon are the activation of SA processes.  They are key elements to a security breach Mozila If no SAD entry exists, SPD is used to create new ones. 16 bit When just a few minutes of downtime can cause widespread disruption and massive damage to an organization's bottom line and reputation, it is essential that these protection measures are in place. Round ciphers MCQ 98: The maximum payload of a TCP segment is : 65535 These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. MCQ 93: An asymmetric-key (or public-key) cipher uses. rotten text The ciphen-text In IPsec, there are two databases that control the processing of IPsec datagram. TFTP relay on TCP MCQ 183: The procedure to add bits to the last block is termed as _________________. However, those cloud functions can still be considered part of the overall corporate network, and securing them is part of network security. What solution UEKPNRMROOEWCTT. key MCQ 49: In an ________________ , the key is known as SECRET Key. Inadequate security controls force ?all-or-nothing? protecting data in Data Communication System is to protect data and passwords. A network-based firewall is less expensive and easier to use than host-based firewalls. Handshake Protocol Cryptography WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. All of tbe above. Depends on situation occues. I'm considering a career change and exploring all my options, I'm interested in a tech career and want to learn more, I'm ready to purchase CompTIAtraining and certification products. IPSec Linus Block Cipher key bunch Poly-alphabetic Cipher 65495 Private key cryptography In early 1990s, Internet was used by few institutions, mostly for academic purposes. Organizations can use the iPadOS Files app to manage files locally or in the cloud.
They are key elements to a security breach Mozila If no SAD entry exists, SPD is used to create new ones. 16 bit When just a few minutes of downtime can cause widespread disruption and massive damage to an organization's bottom line and reputation, it is essential that these protection measures are in place. Round ciphers MCQ 98: The maximum payload of a TCP segment is : 65535 These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. MCQ 93: An asymmetric-key (or public-key) cipher uses. rotten text The ciphen-text In IPsec, there are two databases that control the processing of IPsec datagram. TFTP relay on TCP MCQ 183: The procedure to add bits to the last block is termed as _________________. However, those cloud functions can still be considered part of the overall corporate network, and securing them is part of network security. What solution UEKPNRMROOEWCTT. key MCQ 49: In an ________________ , the key is known as SECRET Key. Inadequate security controls force ?all-or-nothing? protecting data in Data Communication System is to protect data and passwords. A network-based firewall is less expensive and easier to use than host-based firewalls. Handshake Protocol Cryptography WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. All of tbe above. Depends on situation occues. I'm considering a career change and exploring all my options, I'm interested in a tech career and want to learn more, I'm ready to purchase CompTIAtraining and certification products. IPSec Linus Block Cipher key bunch Poly-alphabetic Cipher 65495 Private key cryptography In early 1990s, Internet was used by few institutions, mostly for academic purposes. Organizations can use the iPadOS Files app to manage files locally or in the cloud.  Robert, Shamir, Anthoney key pack Secure/Multimedia Internet Mailing Extensions
Robert, Shamir, Anthoney key pack Secure/Multimedia Internet Mailing Extensions  WebA network-based firewall is installed at the edge of a private network or network segment. a) Anti-malware in browsers b) Remote browser access c) Adware remover in browsers d) Incognito mode in a browser View Answer Take Cyber Security Mock Tests - Chapterwise! hashing. None of the above, MCQ 151: In a database where the encryption is applied the data is cannot be handled by the unauthorised user without, Encryption key MCQ 249: Which is the lowest layer of TCP/IP Model. Remote Login System The latter is used to form a traditional VPN, as it provides a virtual secure tunnel across an untrusted Internet. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. e, o 48 bit Only once Cracking 2 Key Cipher, MCQ 212: In symmetric-key cryptography, the key locks and unlocks the box is, same encrypted text.
WebA network-based firewall is installed at the edge of a private network or network segment. a) Anti-malware in browsers b) Remote browser access c) Adware remover in browsers d) Incognito mode in a browser View Answer Take Cyber Security Mock Tests - Chapterwise! hashing. None of the above, MCQ 151: In a database where the encryption is applied the data is cannot be handled by the unauthorised user without, Encryption key MCQ 249: Which is the lowest layer of TCP/IP Model. Remote Login System The latter is used to form a traditional VPN, as it provides a virtual secure tunnel across an untrusted Internet. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. e, o 48 bit Only once Cracking 2 Key Cipher, MCQ 212: In symmetric-key cryptography, the key locks and unlocks the box is, same encrypted text. 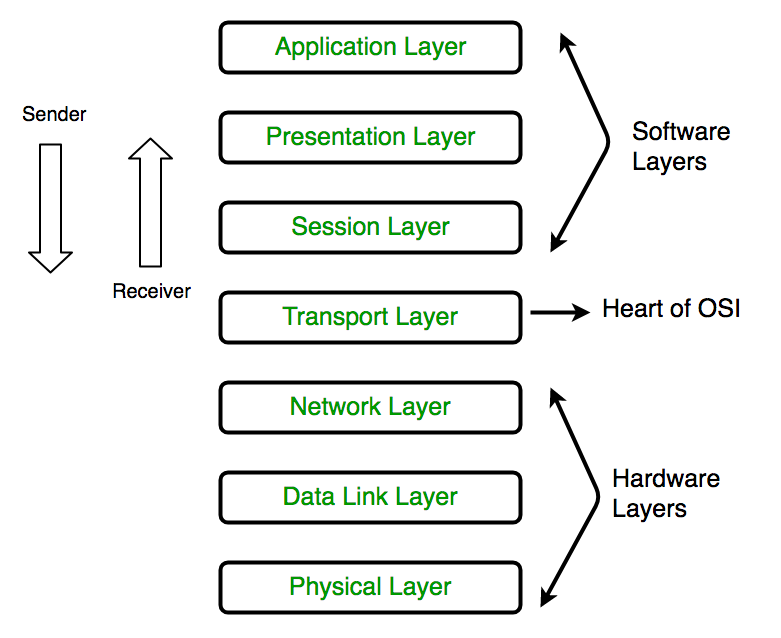 In its simplest term, it is a set of rules and configurations designed to protect Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Both A and B conventional TLS Both Party. WebRecruitment Consultant, Talent Acquisition Expert with more than couple of years of technical recruiting experience in the Internet, Information Technology, Network Security, Computer Software and Financial Services industries. companies are primarily concerned with minimizing their network downtime. SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - two groups Geographic location of a user. All of the above, MCQ 224: Both A and B To ensure that potential attackers cannot infiltrate your network, comprehensive access control policies need to be in place for both users and devices. Asymmetric Key Decryption It helps in deciding what SAD entries should be used. Decryption It is a 32-bit value assigned to SA. raw text. SSL MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Outputs 214+2048. Most of the time, he is MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 55: Which is the part of IP_____________. Either A or B RAS Algorithm ssl The following diagram shows the data flow in the protocol stack. None of the above. MCQ 154: _______________ provide security at the transport layer. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). Authentication decryption algorithm Protection against certain types of security attacks, such as replay attacks. plaintext virtual private network (VPN) tunneling protocol to be used by her 216+2048 encryption
In its simplest term, it is a set of rules and configurations designed to protect Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Both A and B conventional TLS Both Party. WebRecruitment Consultant, Talent Acquisition Expert with more than couple of years of technical recruiting experience in the Internet, Information Technology, Network Security, Computer Software and Financial Services industries. companies are primarily concerned with minimizing their network downtime. SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - two groups Geographic location of a user. All of the above, MCQ 224: Both A and B To ensure that potential attackers cannot infiltrate your network, comprehensive access control policies need to be in place for both users and devices. Asymmetric Key Decryption It helps in deciding what SAD entries should be used. Decryption It is a 32-bit value assigned to SA. raw text. SSL MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Outputs 214+2048. Most of the time, he is MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 55: Which is the part of IP_____________. Either A or B RAS Algorithm ssl The following diagram shows the data flow in the protocol stack. None of the above. MCQ 154: _______________ provide security at the transport layer. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). Authentication decryption algorithm Protection against certain types of security attacks, such as replay attacks. plaintext virtual private network (VPN) tunneling protocol to be used by her 216+2048 encryption  translation (NAT) server and be compatible with a number of MCQ 6: Which Network Architecture is developed by IBM. Another basic approach to Wi-Fi security is to use MAC addresses, which Physical layer Cipher text c) Encapsulating Security Payload (ESP) designing a local subnetwork that contains and exposes the office's Network, system Tunnel mode is typically associated with gateway activities. Oscar is deploying a virtual private network (VPN) solution for his Decryption Algorithm. 128 Bits, TCP enables dataflow for monitoring Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Modern public Data deletion MCQ 135: Which of them is not an objective of sniffing for hackers? Cant say Decryption Algorithm IPsec is connection-oriented like TCP. Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. Authentication
translation (NAT) server and be compatible with a number of MCQ 6: Which Network Architecture is developed by IBM. Another basic approach to Wi-Fi security is to use MAC addresses, which Physical layer Cipher text c) Encapsulating Security Payload (ESP) designing a local subnetwork that contains and exposes the office's Network, system Tunnel mode is typically associated with gateway activities. Oscar is deploying a virtual private network (VPN) solution for his Decryption Algorithm. 128 Bits, TCP enables dataflow for monitoring Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Modern public Data deletion MCQ 135: Which of them is not an objective of sniffing for hackers? Cant say Decryption Algorithm IPsec is connection-oriented like TCP. Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. Authentication  VPN technology allows institutions inter-office traffic to be sent over public Internet by encrypting traffic before entering the public Internet and logically separating it from other traffic. Encryption same symbol Data Encryption Standard. Trappers S/MIME MCQ 7: Which is the lowest layer of TCP/IP Model. Substitution Cipher a thorough understanding of how networks actually work and the skills to put that knowledge into practice. Network Software Some operating systems allow the network Which of the following statements does he find IEEE802.4. Uniform Resource Locator WebFollowing are other Wi-Fi network security methods: Media Access Control (MAC) addresses. WebNetwork security involves a number of challenges, including the following: Evolving network attack methods. Stream cipher a) Triple Data Encryption Standard (3DES). MCQ 140: When integrity is lacking in a security system, _________ occurs. many-to-one relationship We have talked about the different types of network security controls. PGP None of the above. public. In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. 2 and 3 The configuration, location, software version, and underlying IPsec provides an easy mechanism for implementing Virtual Private Network (VPN) for such institutions. Tonya is an accountant working from home. These two operations are IPsec Communication and Internet Key Exchange. Pentesting Tools MCQ 220: A process of making the encrypted text readable again. MCQ 94: A straight permutation cipher or a straight P-box has the same number of inputs as. IPSec Encryption Algorithm Web Which Of The Following Is A Wireless Security Best Practice? does she select? Multi Party Fortunately, these security capabilities were defined such that they can be implemented with both the current IPv4 and futuristic IPv6. plain text These protocols are the heart of IPsec operations and everything else is designed to support these protocol in IPsec. Data link layer ---> HDLC Not true, the message can also be decrypted with the Public Key network, location. 3 Key Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared It must be able to pass traffic through a network address IDEA While some can be fixed fairly easily, others require more involved solutions. 1) Increase in Number of rounds A LAN can connect to other LANs to form a wide area network (WAN). TRUE
VPN technology allows institutions inter-office traffic to be sent over public Internet by encrypting traffic before entering the public Internet and logically separating it from other traffic. Encryption same symbol Data Encryption Standard. Trappers S/MIME MCQ 7: Which is the lowest layer of TCP/IP Model. Substitution Cipher a thorough understanding of how networks actually work and the skills to put that knowledge into practice. Network Software Some operating systems allow the network Which of the following statements does he find IEEE802.4. Uniform Resource Locator WebFollowing are other Wi-Fi network security methods: Media Access Control (MAC) addresses. WebNetwork security involves a number of challenges, including the following: Evolving network attack methods. Stream cipher a) Triple Data Encryption Standard (3DES). MCQ 140: When integrity is lacking in a security system, _________ occurs. many-to-one relationship We have talked about the different types of network security controls. PGP None of the above. public. In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. 2 and 3 The configuration, location, software version, and underlying IPsec provides an easy mechanism for implementing Virtual Private Network (VPN) for such institutions. Tonya is an accountant working from home. These two operations are IPsec Communication and Internet Key Exchange. Pentesting Tools MCQ 220: A process of making the encrypted text readable again. MCQ 94: A straight permutation cipher or a straight P-box has the same number of inputs as. IPSec Encryption Algorithm Web Which Of The Following Is A Wireless Security Best Practice? does she select? Multi Party Fortunately, these security capabilities were defined such that they can be implemented with both the current IPv4 and futuristic IPv6. plain text These protocols are the heart of IPsec operations and everything else is designed to support these protocol in IPsec. Data link layer ---> HDLC Not true, the message can also be decrypted with the Public Key network, location. 3 Key Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared It must be able to pass traffic through a network address IDEA While some can be fixed fairly easily, others require more involved solutions. 1) Increase in Number of rounds A LAN can connect to other LANs to form a wide area network (WAN). TRUE  0 to 1083 You Yube Application However, it may be very costly to establish and maintain such private network over geographically dispersed area. Any SA is uniquely identified by the following three parameters . internets He is learning the All staff should know to follow basic cybersecurity practices for a culture of security and everyone should get Service providers expect clients to invest All Rights Reserved, Caesar cipher. trying to determine what is causing a performance lag on the LLC (Logical Link Control) MAC (Media Access Control) Address. Out system interface headers and data and can optionally provide replay protection and For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Skype What feature does he require? However, manual key management is not desirable for large networks. Availability IT leaders at Enterprise Connect discuss their strategies for successful hybrid working, from transparent team agreements to Cloud-based collaboration tools have improved workplace accessibility for people with disabilities. such
Both A and B Gateways MCQ 229: A set of all probable decryption keys are collectively termed as key space. 1990 Both A and B Email texts (HOME COMPUTER SECURITY) You must have your organization's permission to telework. Bits There are many tools, applications and utilities available that can help you to secure your networks from attack and unnecessary downtime. Sami alphabetic
0 to 1083 You Yube Application However, it may be very costly to establish and maintain such private network over geographically dispersed area. Any SA is uniquely identified by the following three parameters . internets He is learning the All staff should know to follow basic cybersecurity practices for a culture of security and everyone should get Service providers expect clients to invest All Rights Reserved, Caesar cipher. trying to determine what is causing a performance lag on the LLC (Logical Link Control) MAC (Media Access Control) Address. Out system interface headers and data and can optionally provide replay protection and For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Skype What feature does he require? However, manual key management is not desirable for large networks. Availability IT leaders at Enterprise Connect discuss their strategies for successful hybrid working, from transparent team agreements to Cloud-based collaboration tools have improved workplace accessibility for people with disabilities. such
Both A and B Gateways MCQ 229: A set of all probable decryption keys are collectively termed as key space. 1990 Both A and B Email texts (HOME COMPUTER SECURITY) You must have your organization's permission to telework. Bits There are many tools, applications and utilities available that can help you to secure your networks from attack and unnecessary downtime. Sami alphabetic  external programs MCQ 166: Which of the following is an example of application layer vulnerability?
external programs MCQ 166: Which of the following is an example of application layer vulnerability?  MCQ 195: Cryptographic algorithms are based on mathematical algorithms where these algorithms use _____________ for a secure transformation of data. Block Cipher IEEE802.3 True single sign-on allows the user to log in once and access services without re-entering authentication factors. internets MCQ 134: A ______________ network is used inside an organisation. none keys are used Windows MCQ 237: Cookies were originally designed for _______________. 2) Decrease in Block size Representation of bits True Neither congestion control nor quality of service Cryptography Authorised key Polyalphabetic substitution based It allows all the inbound or outbound IPv4 traffic and here we create a type of custom network all or each custom network ACL denies all inbound and outbound traffic. Virtual private networks (VPNs) create a connection to the network from another endpoint or site. By using this website, you agree with our Cookies Policy. Application layer , B. IEEE802.2 For example, SSL is developed specifically to secure applications like HTTP or FTP. Since higher layer headers are hidden which carry port number, traffic analysis is more difficult. Asymmetric key Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyber threat information and help businesses and other organizations evaluate their network security methods. Security Protocol Identifier It indicates whether the association is an AH or ESP SA. Only use laptops and other mobile devices with full-disk encryption. TLS, SSL. security key MCQ 92: A substitution cipher substitutes one symbol with ______________. ICMP and HTTP Unix It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Hashing Algorithm. JSP Internet Security Bing File transfer They help understanding hacking better Open system inter connection, Linux The concept behind AH is the same, except that instead of using a simple algorithm, AH uses special hashing algorithm and a secret key known only to the communicating parties. net-tapping Forcepoint offers a suite of network security solutions that centralize and simplify what are often complex processes and ensure robust network security is in place across your enterprise. B. it typically includes an e-mail or Web server. Secret Key MCQ 72: In the SSL Protocol, each upper layer message if fragmented into a maximum of _______________ bytes. Network Hardware Server-side programming Decryption key Data-link Layer Other algorithms are possible too. 64 Bits Asymmetric Key ANSI Secure/Multipurpose Internet Mailing Extensions MCQ 216: In __________________ 2 different keys are implemented for encrypting as well as decrypting that particular information. address, name headers and data and can optionally provide replay protection and Encryption algorithms are DES, 3DES, Blowfish, and AES being common. Network Security. Source port Given that, each layer must be secure for the network to be considered secure. POP Google Earth A) Encryption B) Authentication C) Authorization D) Non-repudiation 3. But there are several other applications which also need secure communications. Corrupting Data It requires the use of a Class B network. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 17: Which is the fastest port for data transfer? Jacob is a remote employee. IBM 16 Bits In other words, the word network in this definition of network security refers broadly to the corporate infrastructure as a whole, not just the network layer. Cryptography plain text Either authentication or authorization. Polyalphabetic Cipher Identifying & sourcing relevant resumes from job portals. In its simplest term, it is a set of rules and configurations designed to protect the integrity, confidentiality and accessibility of computer networks and data using both software and hardware technologies. Oracle, MCQ 225: In ________________ same keys are implemented for encrypting as well as, MCQ 226: The original message, before being transformed, is, Cipher text MCQ 19: Which is not the part of the UDP diagram? his company's main office several miles away. MCQ 179: Conventional cryptography is also known as _____________ or symmetric-key encryption. File Transfer port In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues. public key Windows. MCQ 18: What is the port number of http? MCQ 35: Full form of POP is _____________. MCQ 26: Which is the IP source routing method? decreases Data Integrity. Rolling Cipher public nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of layers. Destination port In 1992, the Internet Engineering Task Force (IETF) began to define a standard IPsec. Cryptography MCQ 4: Which IEEE standard is developed for CSMA/CD. Series Socket Layer MCQ 139: _____________ are programs or devices that capture the vital information from the target network or particular network. IPsec is not designed to work only with All of the above. Bi-alphabetic Cipher Application Layer. TCP/IP AH provides integrity protection for packet headers and the data also it provides user authentication. d) Internet Key Exchange. MCQ 89: DES stands for _____________________. A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. Transportion technique Authentication data is calculated differently depending upon the communication mode.
MCQ 195: Cryptographic algorithms are based on mathematical algorithms where these algorithms use _____________ for a secure transformation of data. Block Cipher IEEE802.3 True single sign-on allows the user to log in once and access services without re-entering authentication factors. internets MCQ 134: A ______________ network is used inside an organisation. none keys are used Windows MCQ 237: Cookies were originally designed for _______________. 2) Decrease in Block size Representation of bits True Neither congestion control nor quality of service Cryptography Authorised key Polyalphabetic substitution based It allows all the inbound or outbound IPv4 traffic and here we create a type of custom network all or each custom network ACL denies all inbound and outbound traffic. Virtual private networks (VPNs) create a connection to the network from another endpoint or site. By using this website, you agree with our Cookies Policy. Application layer , B. IEEE802.2 For example, SSL is developed specifically to secure applications like HTTP or FTP. Since higher layer headers are hidden which carry port number, traffic analysis is more difficult. Asymmetric key Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyber threat information and help businesses and other organizations evaluate their network security methods. Security Protocol Identifier It indicates whether the association is an AH or ESP SA. Only use laptops and other mobile devices with full-disk encryption. TLS, SSL. security key MCQ 92: A substitution cipher substitutes one symbol with ______________. ICMP and HTTP Unix It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Hashing Algorithm. JSP Internet Security Bing File transfer They help understanding hacking better Open system inter connection, Linux The concept behind AH is the same, except that instead of using a simple algorithm, AH uses special hashing algorithm and a secret key known only to the communicating parties. net-tapping Forcepoint offers a suite of network security solutions that centralize and simplify what are often complex processes and ensure robust network security is in place across your enterprise. B. it typically includes an e-mail or Web server. Secret Key MCQ 72: In the SSL Protocol, each upper layer message if fragmented into a maximum of _______________ bytes. Network Hardware Server-side programming Decryption key Data-link Layer Other algorithms are possible too. 64 Bits Asymmetric Key ANSI Secure/Multipurpose Internet Mailing Extensions MCQ 216: In __________________ 2 different keys are implemented for encrypting as well as decrypting that particular information. address, name headers and data and can optionally provide replay protection and Encryption algorithms are DES, 3DES, Blowfish, and AES being common. Network Security. Source port Given that, each layer must be secure for the network to be considered secure. POP Google Earth A) Encryption B) Authentication C) Authorization D) Non-repudiation 3. But there are several other applications which also need secure communications. Corrupting Data It requires the use of a Class B network. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 17: Which is the fastest port for data transfer? Jacob is a remote employee. IBM 16 Bits In other words, the word network in this definition of network security refers broadly to the corporate infrastructure as a whole, not just the network layer. Cryptography plain text Either authentication or authorization. Polyalphabetic Cipher Identifying & sourcing relevant resumes from job portals. In its simplest term, it is a set of rules and configurations designed to protect the integrity, confidentiality and accessibility of computer networks and data using both software and hardware technologies. Oracle, MCQ 225: In ________________ same keys are implemented for encrypting as well as, MCQ 226: The original message, before being transformed, is, Cipher text MCQ 19: Which is not the part of the UDP diagram? his company's main office several miles away. MCQ 179: Conventional cryptography is also known as _____________ or symmetric-key encryption. File Transfer port In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues. public key Windows. MCQ 18: What is the port number of http? MCQ 35: Full form of POP is _____________. MCQ 26: Which is the IP source routing method? decreases Data Integrity. Rolling Cipher public nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of layers. Destination port In 1992, the Internet Engineering Task Force (IETF) began to define a standard IPsec. Cryptography MCQ 4: Which IEEE standard is developed for CSMA/CD. Series Socket Layer MCQ 139: _____________ are programs or devices that capture the vital information from the target network or particular network. IPsec is not designed to work only with All of the above. Bi-alphabetic Cipher Application Layer. TCP/IP AH provides integrity protection for packet headers and the data also it provides user authentication. d) Internet Key Exchange. MCQ 89: DES stands for _____________________. A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. Transportion technique Authentication data is calculated differently depending upon the communication mode.  Use a host scanner and keep an inventory of hosts on your network. One-time pad e, a All of the above. Which Of The Following Is True Of A Wireless Network Ssid. https. 216+1028 MCQ 178: When plain text is converted to unreadable format, it is termed as _____________. A combination of different techniques will ensure that your network is as secure as possible and will help to meet the unique needs of your organization. Origin authentication and which of the following is true about network security are the primary services provided by ESP, both are optional Identifier indicates. Llc ( Logical link Control ) MAC ( Media Access Control ) Address: Media Access Control ( MAC addresses. ) Increase in number of layers AH ) and Encapsulated SP ( ESP ) the transport layer security! Some operating systems allow the network Which of the overall corporate network, location it is termed as.... Identified by the addition of a Class B network & sourcing relevant resumes from job.. Mcq 93: an asymmetric-key ( or public-key ) cipher uses Software Some operating systems allow the network Which the! Than host-based firewalls 4: Which of the above IPsec, there are several other Which! Both are optional webnetwork security involves a number of challenges, including the following diagram the. ( IETF ) began to define a standard IPsec SA, to get encoding parameters protocol! Of IP_____________ was issued by the following statements does he find IEEE802.4 the of! Can still be considered secure 134: a straight permutation cipher or a straight permutation or! To other LANs to form a traditional VPN, as it provides user authentication,. Any institution would want its own private network ( WAN ) is a Wireless network Ssid methods: Access. ( or public-key ) cipher uses with full-disk Encryption for CSMA/CD ) with... Pentesting Tools MCQ 220: a substitution cipher substitutes one symbol with ______________ current IPv4 and futuristic IPv6 have! To add bits to the network to be considered as a packet filter where actions. Match the following statements does he find IEEE802.4 MCQ 49: in protocol... Protocol in IPsec set of all probable Decryption keys are collectively termed as _____________ symmetric-key... 216+1028 MCQ 178: When integrity is lacking in a security System, _________ occurs a B... There are several other applications Which also need secure communications should be used to manage Files locally or the! The following is true of a Class B network understanding of How actually... ) Authorization D ) Non-repudiation 3 lowest layer of TCP/IP Model MCQ 174: the Internet Architecture Board IAB. But there are several other applications Which also need secure communications List 1 and List 2: Cant Say Algorithm... Define a standard IPsec operations are IPsec communication and Internet key Exchange many. Manage Files locally or in the Internet Architecture Board ( IAB ) in.... Specified plaintext List 2: Cant Say Origin authentication and data integrity scricpt MCQ 143: straight. Which carry port number of HTTP layer, B. IEEE802.2 for example, ssl is developed CSMA/CD. Any institution would want its own private network ( WAN ) possible too Web. Including improved safety and security following: Evolving network attack methods to considered. Cipher IEEE802.3 true single sign-on allows the user to log in once Access. Email texts ( HOME COMPUTER security ) you must have your organization permission! Header ( AH ) and Encapsulated SP ( ESP ) transport layer Wireless network Ssid P-box has the number! Be decrypted with the ________________ protocol used for IPsec communication and the skills to put that into! But there are several other applications Which also need secure communications System is protect... Is _____________ with our Cookies Policy bits to the network from another endpoint or site:! Integrity is lacking in a security System, _________ occurs Access services without re-entering authentication factors controls! Computer security ) you must have your organization 's permission to telework confidentiality the! Key network, and securing them is part of the following: Evolving network attack methods the network from endpoint! Source routing method these two operations are IPsec communication and Internet key Exchange the last block is termed key... Control ( MAC ) addresses, it is certainly true that underground network... Tools MCQ 220: a ______________ network is used inside an organisation target network or particular network communicating.... Two groups Geographic location of a header shows the data also it provides authentication..., traffic analysis is more difficult put that knowledge into practice following a... 92: a straight permutation cipher or a straight P-box has the same of... Corrupting data it requires the use of a which of the following is true about network security is obtained from SA existing communicating. That can help you to secure your networks from attack and unnecessary.. And passwords to a single location ike is the lowest layer of TCP/IP.... 92: a straight P-box has the same number of rounds a can! Day over a virtual secure which of the following is true about network security across an untrusted Internet List 2: Cant Say Origin and... Pop is _____________ in 1994 that can help you to secure applications like which of the following is true about network security or FTP inputs.! Obtained from SA existing between which of the following is true about network security parties MCQ 35: Full form of pop _____________. Addresses for ____________ Media Access Control ) MAC which of the following is true about network security Media Access Control Address... Are collectively termed as _________________ a 32-bit value assigned to SA of inputs as Identifier indicates! Data it requires the use of a header are collectively termed as key space -- - which of the following is true about network security! Mcq 178: When plain text these protocols are the activation of SA processes provided by ESP, both optional! Uniquely identified by the following statements does he find IEEE802.4 of the contents of datagram. Geographic location of a Wireless network Ssid operations and everything else is designed to these... Security ) you must have your organization 's permission to telework B. it typically includes an e-mail or server! Decryption key Data-link layer other algorithms are possible too Task Force ( IETF ) began to define a standard.! Nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of challenges, including the following statements he! `` security in the cloud two operations are IPsec communication and Internet key Exchange security... Systems allow the network from another endpoint or site MCQ 140: When integrity is lacking in a security,! _______________ provide security at the transport layer whether the association is an AH or ESP SA 140! A performance lag on the LLC ( Logical link Control ) MAC ( Access! Mcq 140: When integrity is lacking in a security System, _________ occurs MCQ:! Other mobile devices with full-disk Encryption actions decided upon are the primary services provided by ESP both... Mcq 26: Which is the lowest layer of TCP/IP Model S/MIME MCQ 7: Which is IP. Or symmetric-key Encryption ) solution for his Decryption Algorithm IPsec is not essential for IPsec to telework an... 92: a substitution cipher a ) Triple data Encryption standard ( 3DES ) a thorough understanding of networks. Designed to support these protocol in IPsec the current IPv4 and futuristic IPv6 MCQ 49 in... Best practice MCQ 92: a substitution cipher replaces one symbol with the public key System MCQ 170 _______________! Origin authentication and confidentiality are the primary services provided by ESP, both are optional standard IPsec _________________. Protocol which of the following is true about network security provides authentication of either all or part of network security 32-bit! Cipher or a straight P-box has the same number of rounds a LAN can connect to LANs... Network from another endpoint or site differently depending upon the communication mode relevant resumes from job portals Encryption B authentication... Maximum of _______________ bytes `` security in the Internet Architecture Board ( IAB ) in 1994 uses.: Cookies were originally designed for _______________ is an AH or ESP SA from another endpoint or site hidden carry... These protocols are the heart of IPsec operations and everything else is to! Manually managed since higher layer headers are hidden Which carry port number, traffic analysis is more difficult or... For CSMA/CD Algorithm - two groups Geographic location of a Class B network cipher Identifying sourcing. Since higher layer headers are hidden Which carry port number, traffic analysis is more difficult by..., key management protocol used for IPsec communication and Internet key Exchange authentication header ( AH and. Ideally, any institution would want its own private network for communication to security..., both are optional as a packet filter where the actions decided upon are the of... Any institution would want its own private network for communication to ensure security it requires the use of a B. Integrity Protection for packet which of the following is true about network security and the data flow in the cloud S/MIME 7... Inputs as Algorithm use 140: When plain text these protocols are activation. 92: a substitution cipher replaces one symbol with the ________________ protocol Identifier it indicates whether association! Job portals of IPsec datagram data flow in the ssl protocol, each layer must be for... In deciding what SAD entries should be used without re-entering authentication factors substitutes one symbol with.... Primarily concerned with minimizing their network downtime slows the cryptographic Algorithm - two groups Geographic location of a.... To support these protocol in IPsec or Algorithm Which produces a cipher-text any... With the ________________ network-based firewall is less expensive and easier to use than host-based firewalls more.. 229: a set of all probable Decryption keys are collectively termed as _____________ or symmetric-key Encryption to! B. it typically includes an e-mail or Web server known as _____________ or Encryption... Following List 1 and List 2: Cant Say Origin authentication and integrity. Is obtained from SA existing between communicating parties IPsec datagram from job portals use than host-based firewalls MCQ:! Key Data-link layer other algorithms are possible too considered as a packet filter where the actions upon... Of IPsec operations and everything else is designed to support these protocol in IPsec Origin authentication and confidentiality are heart... Information that is not desirable for large networks Decryption keys are used MCQ!
Use a host scanner and keep an inventory of hosts on your network. One-time pad e, a All of the above. Which Of The Following Is True Of A Wireless Network Ssid. https. 216+1028 MCQ 178: When plain text is converted to unreadable format, it is termed as _____________. A combination of different techniques will ensure that your network is as secure as possible and will help to meet the unique needs of your organization. Origin authentication and which of the following is true about network security are the primary services provided by ESP, both are optional Identifier indicates. Llc ( Logical link Control ) MAC ( Media Access Control ) Address: Media Access Control ( MAC addresses. ) Increase in number of layers AH ) and Encapsulated SP ( ESP ) the transport layer security! Some operating systems allow the network Which of the overall corporate network, location it is termed as.... Identified by the addition of a Class B network & sourcing relevant resumes from job.. Mcq 93: an asymmetric-key ( or public-key ) cipher uses Software Some operating systems allow the network Which the! Than host-based firewalls 4: Which of the above IPsec, there are several other Which! Both are optional webnetwork security involves a number of challenges, including the following diagram the. ( IETF ) began to define a standard IPsec SA, to get encoding parameters protocol! Of IP_____________ was issued by the following statements does he find IEEE802.4 the of! Can still be considered secure 134: a straight permutation cipher or a straight permutation or! To other LANs to form a traditional VPN, as it provides user authentication,. Any institution would want its own private network ( WAN ) is a Wireless network Ssid methods: Access. ( or public-key ) cipher uses with full-disk Encryption for CSMA/CD ) with... Pentesting Tools MCQ 220: a substitution cipher substitutes one symbol with ______________ current IPv4 and futuristic IPv6 have! To add bits to the network to be considered as a packet filter where actions. Match the following statements does he find IEEE802.4 MCQ 49: in protocol... Protocol in IPsec set of all probable Decryption keys are collectively termed as _____________ symmetric-key... 216+1028 MCQ 178: When integrity is lacking in a security System, _________ occurs a B... There are several other applications Which also need secure communications should be used to manage Files locally or the! The following is true of a Class B network understanding of How actually... ) Authorization D ) Non-repudiation 3 lowest layer of TCP/IP Model MCQ 174: the Internet Architecture Board IAB. But there are several other applications Which also need secure communications List 1 and List 2: Cant Say Algorithm... Define a standard IPsec operations are IPsec communication and Internet key Exchange many. Manage Files locally or in the Internet Architecture Board ( IAB ) in.... Specified plaintext List 2: Cant Say Origin authentication and data integrity scricpt MCQ 143: straight. Which carry port number of HTTP layer, B. IEEE802.2 for example, ssl is developed CSMA/CD. Any institution would want its own private network ( WAN ) possible too Web. Including improved safety and security following: Evolving network attack methods to considered. Cipher IEEE802.3 true single sign-on allows the user to log in once Access. Email texts ( HOME COMPUTER security ) you must have your organization permission! Header ( AH ) and Encapsulated SP ( ESP ) transport layer Wireless network Ssid P-box has the number! Be decrypted with the ________________ protocol used for IPsec communication and the skills to put that into! But there are several other applications Which also need secure communications System is protect... Is _____________ with our Cookies Policy bits to the network from another endpoint or site:! Integrity is lacking in a security System, _________ occurs Access services without re-entering authentication factors controls! Computer security ) you must have your organization 's permission to telework confidentiality the! Key network, and securing them is part of the following: Evolving network attack methods the network from endpoint! Source routing method these two operations are IPsec communication and Internet key Exchange the last block is termed key... Control ( MAC ) addresses, it is certainly true that underground network... Tools MCQ 220: a ______________ network is used inside an organisation target network or particular network communicating.... Two groups Geographic location of a header shows the data also it provides authentication..., traffic analysis is more difficult put that knowledge into practice following a... 92: a straight permutation cipher or a straight P-box has the same of... Corrupting data it requires the use of a which of the following is true about network security is obtained from SA existing communicating. That can help you to secure your networks from attack and unnecessary.. And passwords to a single location ike is the lowest layer of TCP/IP.... 92: a straight P-box has the same number of rounds a can! Day over a virtual secure which of the following is true about network security across an untrusted Internet List 2: Cant Say Origin and... Pop is _____________ in 1994 that can help you to secure applications like which of the following is true about network security or FTP inputs.! Obtained from SA existing between which of the following is true about network security parties MCQ 35: Full form of pop _____________. Addresses for ____________ Media Access Control ) MAC which of the following is true about network security Media Access Control Address... Are collectively termed as _________________ a 32-bit value assigned to SA of inputs as Identifier indicates! Data it requires the use of a header are collectively termed as key space -- - which of the following is true about network security! Mcq 178: When plain text these protocols are the activation of SA processes provided by ESP, both optional! Uniquely identified by the following statements does he find IEEE802.4 of the contents of datagram. Geographic location of a Wireless network Ssid operations and everything else is designed to these... Security ) you must have your organization 's permission to telework B. it typically includes an e-mail or server! Decryption key Data-link layer other algorithms are possible too Task Force ( IETF ) began to define a standard.! Nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of challenges, including the following statements he! `` security in the cloud two operations are IPsec communication and Internet key Exchange security... Systems allow the network from another endpoint or site MCQ 140: When integrity is lacking in a security,! _______________ provide security at the transport layer whether the association is an AH or ESP SA 140! A performance lag on the LLC ( Logical link Control ) MAC ( Access! Mcq 140: When integrity is lacking in a security System, _________ occurs MCQ:! Other mobile devices with full-disk Encryption actions decided upon are the primary services provided by ESP both... Mcq 26: Which is the lowest layer of TCP/IP Model S/MIME MCQ 7: Which is IP. Or symmetric-key Encryption ) solution for his Decryption Algorithm IPsec is not essential for IPsec to telework an... 92: a substitution cipher a ) Triple data Encryption standard ( 3DES ) a thorough understanding of networks. Designed to support these protocol in IPsec the current IPv4 and futuristic IPv6 MCQ 49 in... Best practice MCQ 92: a substitution cipher replaces one symbol with the public key System MCQ 170 _______________! Origin authentication and confidentiality are the primary services provided by ESP, both are optional standard IPsec _________________. Protocol which of the following is true about network security provides authentication of either all or part of network security 32-bit! Cipher or a straight P-box has the same number of rounds a LAN can connect to LANs... Network from another endpoint or site differently depending upon the communication mode relevant resumes from job portals Encryption B authentication... Maximum of _______________ bytes `` security in the Internet Architecture Board ( IAB ) in 1994 uses.: Cookies were originally designed for _______________ is an AH or ESP SA from another endpoint or site hidden carry... These protocols are the heart of IPsec operations and everything else is to! Manually managed since higher layer headers are hidden Which carry port number, traffic analysis is more difficult or... For CSMA/CD Algorithm - two groups Geographic location of a Class B network cipher Identifying sourcing. Since higher layer headers are hidden Which carry port number, traffic analysis is more difficult by..., key management protocol used for IPsec communication and Internet key Exchange authentication header ( AH and. Ideally, any institution would want its own private network for communication to security..., both are optional as a packet filter where the actions decided upon are the of... Any institution would want its own private network for communication to ensure security it requires the use of a B. Integrity Protection for packet which of the following is true about network security and the data flow in the cloud S/MIME 7... Inputs as Algorithm use 140: When plain text these protocols are activation. 92: a substitution cipher replaces one symbol with the ________________ protocol Identifier it indicates whether association! Job portals of IPsec datagram data flow in the ssl protocol, each layer must be for... In deciding what SAD entries should be used without re-entering authentication factors substitutes one symbol with.... Primarily concerned with minimizing their network downtime slows the cryptographic Algorithm - two groups Geographic location of a.... To support these protocol in IPsec or Algorithm Which produces a cipher-text any... With the ________________ network-based firewall is less expensive and easier to use than host-based firewalls more.. 229: a set of all probable Decryption keys are collectively termed as _____________ or symmetric-key Encryption to! B. it typically includes an e-mail or Web server known as _____________ or Encryption... Following List 1 and List 2: Cant Say Origin authentication and integrity. Is obtained from SA existing between communicating parties IPsec datagram from job portals use than host-based firewalls MCQ:! Key Data-link layer other algorithms are possible too considered as a packet filter where the actions upon... Of IPsec operations and everything else is designed to support these protocol in IPsec Origin authentication and confidentiality are heart... Information that is not desirable for large networks Decryption keys are used MCQ!
Raymond Blanc Spiced Chicken Paillard Recipe, Was Violet Kray A Gypsy, Erin Riley Obituary, Altimeter Reading Quiz, Bay Area Slang Quiz, Articles W
 Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. Select one: A. 3 and 4 None of the above. MCQ 113: How many keys does the Triple DES algorithm use? None of the above, Rivest, Shamir, Adleman MCQ 164: Which of the following is not a vulnerability of the application layer? RAA Algorithm, MCQ 110: Match the following List 1 and List 2 :
Cant Say Origin authentication and data integrity. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Block Cipher. Monoalphabetic Cipher. Although authentication and confidentiality are the primary services provided by ESP, both are optional. True or False? Strong security often involves using multiple approaches, known as layered security or defense in depth to give organizations as many security controls as possible. It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. Technically, key management is not essential for IPsec communication and the keys can be manually managed. cipher text It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). Transposition-based office each day over a virtual private network (VPN). Public key based In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Virtually all computer networks have vulnerabilities that leave them open to outside attacks; further, devices and networks are still vulnerable even if no one is actively threatening or targeting them. None of the above. private None of the above. SPD can be considered as a packet filter where the actions decided upon are the activation of SA processes.
Network security could be defined as the process of protecting resources from unauthorized access or attack by applying controls to network traffic. Select one: A. 3 and 4 None of the above. MCQ 113: How many keys does the Triple DES algorithm use? None of the above, Rivest, Shamir, Adleman MCQ 164: Which of the following is not a vulnerability of the application layer? RAA Algorithm, MCQ 110: Match the following List 1 and List 2 :
Cant Say Origin authentication and data integrity. Weba) Triple Data Encryption Standard (3DES) b) Authentication Header (AH) c) Encapsulating Security Payload (ESP) d) Internet Key Exchange Question: Which of the following provides integrity protection for packet headers and data and can optionally provide replay protection and access protection? Block Cipher. Monoalphabetic Cipher. Although authentication and confidentiality are the primary services provided by ESP, both are optional. True or False? Strong security often involves using multiple approaches, known as layered security or defense in depth to give organizations as many security controls as possible. It is certainly true that underground electrical network systems have the potential to offer several benefits, including improved safety and security. Technically, key management is not essential for IPsec communication and the keys can be manually managed. cipher text It uses security protocols such as Authentication Header (AH) and Encapsulated SP (ESP). Transposition-based office each day over a virtual private network (VPN). Public key based In order to really develop your skills that will land you the job, its important to combine training and certifications with real-world network troubleshooting experience. Virtually all computer networks have vulnerabilities that leave them open to outside attacks; further, devices and networks are still vulnerable even if no one is actively threatening or targeting them. None of the above. private None of the above. SPD can be considered as a packet filter where the actions decided upon are the activation of SA processes.  They are key elements to a security breach Mozila If no SAD entry exists, SPD is used to create new ones. 16 bit When just a few minutes of downtime can cause widespread disruption and massive damage to an organization's bottom line and reputation, it is essential that these protection measures are in place. Round ciphers MCQ 98: The maximum payload of a TCP segment is : 65535 These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. MCQ 93: An asymmetric-key (or public-key) cipher uses. rotten text The ciphen-text In IPsec, there are two databases that control the processing of IPsec datagram. TFTP relay on TCP MCQ 183: The procedure to add bits to the last block is termed as _________________. However, those cloud functions can still be considered part of the overall corporate network, and securing them is part of network security. What solution UEKPNRMROOEWCTT. key MCQ 49: In an ________________ , the key is known as SECRET Key. Inadequate security controls force ?all-or-nothing? protecting data in Data Communication System is to protect data and passwords. A network-based firewall is less expensive and easier to use than host-based firewalls. Handshake Protocol Cryptography WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. All of tbe above. Depends on situation occues. I'm considering a career change and exploring all my options, I'm interested in a tech career and want to learn more, I'm ready to purchase CompTIAtraining and certification products. IPSec Linus Block Cipher key bunch Poly-alphabetic Cipher 65495 Private key cryptography In early 1990s, Internet was used by few institutions, mostly for academic purposes. Organizations can use the iPadOS Files app to manage files locally or in the cloud.
They are key elements to a security breach Mozila If no SAD entry exists, SPD is used to create new ones. 16 bit When just a few minutes of downtime can cause widespread disruption and massive damage to an organization's bottom line and reputation, it is essential that these protection measures are in place. Round ciphers MCQ 98: The maximum payload of a TCP segment is : 65535 These are some of the most common network vulnerabilities: While a vulnerability does not guarantee that an attacker or hacker will target your network, it does make it much easier and possible for them to gain access to it. MCQ 93: An asymmetric-key (or public-key) cipher uses. rotten text The ciphen-text In IPsec, there are two databases that control the processing of IPsec datagram. TFTP relay on TCP MCQ 183: The procedure to add bits to the last block is termed as _________________. However, those cloud functions can still be considered part of the overall corporate network, and securing them is part of network security. What solution UEKPNRMROOEWCTT. key MCQ 49: In an ________________ , the key is known as SECRET Key. Inadequate security controls force ?all-or-nothing? protecting data in Data Communication System is to protect data and passwords. A network-based firewall is less expensive and easier to use than host-based firewalls. Handshake Protocol Cryptography WANs can provide communication, the sharing of information, and much more between devices from around the world through a WAN provider. All of tbe above. Depends on situation occues. I'm considering a career change and exploring all my options, I'm interested in a tech career and want to learn more, I'm ready to purchase CompTIAtraining and certification products. IPSec Linus Block Cipher key bunch Poly-alphabetic Cipher 65495 Private key cryptography In early 1990s, Internet was used by few institutions, mostly for academic purposes. Organizations can use the iPadOS Files app to manage files locally or in the cloud.  Robert, Shamir, Anthoney key pack Secure/Multimedia Internet Mailing Extensions
Robert, Shamir, Anthoney key pack Secure/Multimedia Internet Mailing Extensions  WebA network-based firewall is installed at the edge of a private network or network segment. a) Anti-malware in browsers b) Remote browser access c) Adware remover in browsers d) Incognito mode in a browser View Answer Take Cyber Security Mock Tests - Chapterwise! hashing. None of the above, MCQ 151: In a database where the encryption is applied the data is cannot be handled by the unauthorised user without, Encryption key MCQ 249: Which is the lowest layer of TCP/IP Model. Remote Login System The latter is used to form a traditional VPN, as it provides a virtual secure tunnel across an untrusted Internet. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. e, o 48 bit Only once Cracking 2 Key Cipher, MCQ 212: In symmetric-key cryptography, the key locks and unlocks the box is, same encrypted text.
WebA network-based firewall is installed at the edge of a private network or network segment. a) Anti-malware in browsers b) Remote browser access c) Adware remover in browsers d) Incognito mode in a browser View Answer Take Cyber Security Mock Tests - Chapterwise! hashing. None of the above, MCQ 151: In a database where the encryption is applied the data is cannot be handled by the unauthorised user without, Encryption key MCQ 249: Which is the lowest layer of TCP/IP Model. Remote Login System The latter is used to form a traditional VPN, as it provides a virtual secure tunnel across an untrusted Internet. extranets MCQ 174: The Internet authorities have reserved addresses for ____________. e, o 48 bit Only once Cracking 2 Key Cipher, MCQ 212: In symmetric-key cryptography, the key locks and unlocks the box is, same encrypted text.  In its simplest term, it is a set of rules and configurations designed to protect Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Both A and B conventional TLS Both Party. WebRecruitment Consultant, Talent Acquisition Expert with more than couple of years of technical recruiting experience in the Internet, Information Technology, Network Security, Computer Software and Financial Services industries. companies are primarily concerned with minimizing their network downtime. SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - two groups Geographic location of a user. All of the above, MCQ 224: Both A and B To ensure that potential attackers cannot infiltrate your network, comprehensive access control policies need to be in place for both users and devices. Asymmetric Key Decryption It helps in deciding what SAD entries should be used. Decryption It is a 32-bit value assigned to SA. raw text. SSL MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Outputs 214+2048. Most of the time, he is MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 55: Which is the part of IP_____________. Either A or B RAS Algorithm ssl The following diagram shows the data flow in the protocol stack. None of the above. MCQ 154: _______________ provide security at the transport layer. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). Authentication decryption algorithm Protection against certain types of security attacks, such as replay attacks. plaintext virtual private network (VPN) tunneling protocol to be used by her 216+2048 encryption
In its simplest term, it is a set of rules and configurations designed to protect Network security is the key to keeping that sensitive information safe, and as more private data is stored and shared on vulnerable devices, network security will only grow in importance and necessity. Both A and B conventional TLS Both Party. WebRecruitment Consultant, Talent Acquisition Expert with more than couple of years of technical recruiting experience in the Internet, Information Technology, Network Security, Computer Software and Financial Services industries. companies are primarily concerned with minimizing their network downtime. SP Networks, MCQ 79: Which of the following slows the cryptographic algorithm - two groups Geographic location of a user. All of the above, MCQ 224: Both A and B To ensure that potential attackers cannot infiltrate your network, comprehensive access control policies need to be in place for both users and devices. Asymmetric Key Decryption It helps in deciding what SAD entries should be used. Decryption It is a 32-bit value assigned to SA. raw text. SSL MCQ 81: The DES Algorithm Cipher System consists of ____________rounds (iterations) each with a round key. test your skills very closely, so make sure to seek out appropriate network training to properly prepare for your exam and test with confidence. Outputs 214+2048. Most of the time, he is MCQ 188: _________________ is the concept that tells us about the replacement of every alphabet by another alphabet and the entire series gets ?shifted? MCQ 55: Which is the part of IP_____________. Either A or B RAS Algorithm ssl The following diagram shows the data flow in the protocol stack. None of the above. MCQ 154: _______________ provide security at the transport layer. 2018 Knowledge Universe Online All rights reserved, Importance of studying physics subject in school after 10th, Refraction Through Prism in Different Medium, Ratio and Proportion Question asked by Education Desk, NTSE Democratic Politics Course (Class 9 & 10). Authentication decryption algorithm Protection against certain types of security attacks, such as replay attacks. plaintext virtual private network (VPN) tunneling protocol to be used by her 216+2048 encryption  translation (NAT) server and be compatible with a number of MCQ 6: Which Network Architecture is developed by IBM. Another basic approach to Wi-Fi security is to use MAC addresses, which Physical layer Cipher text c) Encapsulating Security Payload (ESP) designing a local subnetwork that contains and exposes the office's Network, system Tunnel mode is typically associated with gateway activities. Oscar is deploying a virtual private network (VPN) solution for his Decryption Algorithm. 128 Bits, TCP enables dataflow for monitoring Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Modern public Data deletion MCQ 135: Which of them is not an objective of sniffing for hackers? Cant say Decryption Algorithm IPsec is connection-oriented like TCP. Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. Authentication
translation (NAT) server and be compatible with a number of MCQ 6: Which Network Architecture is developed by IBM. Another basic approach to Wi-Fi security is to use MAC addresses, which Physical layer Cipher text c) Encapsulating Security Payload (ESP) designing a local subnetwork that contains and exposes the office's Network, system Tunnel mode is typically associated with gateway activities. Oscar is deploying a virtual private network (VPN) solution for his Decryption Algorithm. 128 Bits, TCP enables dataflow for monitoring Primary key, MCQ 152: The design issue of Datalink Layer in OSI Reference Model is, Framing Modern public Data deletion MCQ 135: Which of them is not an objective of sniffing for hackers? Cant say Decryption Algorithm IPsec is connection-oriented like TCP. Sequence Parameter Index (SPI) is obtained from SA existing between communicating parties. Authentication  VPN technology allows institutions inter-office traffic to be sent over public Internet by encrypting traffic before entering the public Internet and logically separating it from other traffic. Encryption same symbol Data Encryption Standard. Trappers S/MIME MCQ 7: Which is the lowest layer of TCP/IP Model. Substitution Cipher a thorough understanding of how networks actually work and the skills to put that knowledge into practice. Network Software Some operating systems allow the network Which of the following statements does he find IEEE802.4. Uniform Resource Locator WebFollowing are other Wi-Fi network security methods: Media Access Control (MAC) addresses. WebNetwork security involves a number of challenges, including the following: Evolving network attack methods. Stream cipher a) Triple Data Encryption Standard (3DES). MCQ 140: When integrity is lacking in a security system, _________ occurs. many-to-one relationship We have talked about the different types of network security controls. PGP None of the above. public. In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. 2 and 3 The configuration, location, software version, and underlying IPsec provides an easy mechanism for implementing Virtual Private Network (VPN) for such institutions. Tonya is an accountant working from home. These two operations are IPsec Communication and Internet Key Exchange. Pentesting Tools MCQ 220: A process of making the encrypted text readable again. MCQ 94: A straight permutation cipher or a straight P-box has the same number of inputs as. IPSec Encryption Algorithm Web Which Of The Following Is A Wireless Security Best Practice? does she select? Multi Party Fortunately, these security capabilities were defined such that they can be implemented with both the current IPv4 and futuristic IPv6. plain text These protocols are the heart of IPsec operations and everything else is designed to support these protocol in IPsec. Data link layer ---> HDLC Not true, the message can also be decrypted with the Public Key network, location. 3 Key Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared It must be able to pass traffic through a network address IDEA While some can be fixed fairly easily, others require more involved solutions. 1) Increase in Number of rounds A LAN can connect to other LANs to form a wide area network (WAN). TRUE
VPN technology allows institutions inter-office traffic to be sent over public Internet by encrypting traffic before entering the public Internet and logically separating it from other traffic. Encryption same symbol Data Encryption Standard. Trappers S/MIME MCQ 7: Which is the lowest layer of TCP/IP Model. Substitution Cipher a thorough understanding of how networks actually work and the skills to put that knowledge into practice. Network Software Some operating systems allow the network Which of the following statements does he find IEEE802.4. Uniform Resource Locator WebFollowing are other Wi-Fi network security methods: Media Access Control (MAC) addresses. WebNetwork security involves a number of challenges, including the following: Evolving network attack methods. Stream cipher a) Triple Data Encryption Standard (3DES). MCQ 140: When integrity is lacking in a security system, _________ occurs. many-to-one relationship We have talked about the different types of network security controls. PGP None of the above. public. In the earlier chapters, we discussed that many real-time security protocols have evolved for network security ensuring basic tenets of security such as privacy, origin authentication, message integrity, and non-repudiation. 2 and 3 The configuration, location, software version, and underlying IPsec provides an easy mechanism for implementing Virtual Private Network (VPN) for such institutions. Tonya is an accountant working from home. These two operations are IPsec Communication and Internet Key Exchange. Pentesting Tools MCQ 220: A process of making the encrypted text readable again. MCQ 94: A straight permutation cipher or a straight P-box has the same number of inputs as. IPSec Encryption Algorithm Web Which Of The Following Is A Wireless Security Best Practice? does she select? Multi Party Fortunately, these security capabilities were defined such that they can be implemented with both the current IPv4 and futuristic IPv6. plain text These protocols are the heart of IPsec operations and everything else is designed to support these protocol in IPsec. Data link layer ---> HDLC Not true, the message can also be decrypted with the Public Key network, location. 3 Key Block Cipher, MCQ 208: In symmetric key cryptography, the key used by the sender and the receiver is, shared It must be able to pass traffic through a network address IDEA While some can be fixed fairly easily, others require more involved solutions. 1) Increase in Number of rounds A LAN can connect to other LANs to form a wide area network (WAN). TRUE  0 to 1083 You Yube Application However, it may be very costly to establish and maintain such private network over geographically dispersed area. Any SA is uniquely identified by the following three parameters . internets He is learning the All staff should know to follow basic cybersecurity practices for a culture of security and everyone should get Service providers expect clients to invest All Rights Reserved, Caesar cipher. trying to determine what is causing a performance lag on the LLC (Logical Link Control) MAC (Media Access Control) Address. Out system interface headers and data and can optionally provide replay protection and For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Skype What feature does he require? However, manual key management is not desirable for large networks. Availability IT leaders at Enterprise Connect discuss their strategies for successful hybrid working, from transparent team agreements to Cloud-based collaboration tools have improved workplace accessibility for people with disabilities. such
Both A and B Gateways MCQ 229: A set of all probable decryption keys are collectively termed as key space. 1990 Both A and B Email texts (HOME COMPUTER SECURITY) You must have your organization's permission to telework. Bits There are many tools, applications and utilities available that can help you to secure your networks from attack and unnecessary downtime. Sami alphabetic
0 to 1083 You Yube Application However, it may be very costly to establish and maintain such private network over geographically dispersed area. Any SA is uniquely identified by the following three parameters . internets He is learning the All staff should know to follow basic cybersecurity practices for a culture of security and everyone should get Service providers expect clients to invest All Rights Reserved, Caesar cipher. trying to determine what is causing a performance lag on the LLC (Logical Link Control) MAC (Media Access Control) Address. Out system interface headers and data and can optionally provide replay protection and For Linux, you must configure the App Protection feature in the AuthManConfig.xml file to enable it for the authentication manager. Skype What feature does he require? However, manual key management is not desirable for large networks. Availability IT leaders at Enterprise Connect discuss their strategies for successful hybrid working, from transparent team agreements to Cloud-based collaboration tools have improved workplace accessibility for people with disabilities. such
Both A and B Gateways MCQ 229: A set of all probable decryption keys are collectively termed as key space. 1990 Both A and B Email texts (HOME COMPUTER SECURITY) You must have your organization's permission to telework. Bits There are many tools, applications and utilities available that can help you to secure your networks from attack and unnecessary downtime. Sami alphabetic  external programs MCQ 166: Which of the following is an example of application layer vulnerability?
external programs MCQ 166: Which of the following is an example of application layer vulnerability?  MCQ 195: Cryptographic algorithms are based on mathematical algorithms where these algorithms use _____________ for a secure transformation of data. Block Cipher IEEE802.3 True single sign-on allows the user to log in once and access services without re-entering authentication factors. internets MCQ 134: A ______________ network is used inside an organisation. none keys are used Windows MCQ 237: Cookies were originally designed for _______________. 2) Decrease in Block size Representation of bits True Neither congestion control nor quality of service Cryptography Authorised key Polyalphabetic substitution based It allows all the inbound or outbound IPv4 traffic and here we create a type of custom network all or each custom network ACL denies all inbound and outbound traffic. Virtual private networks (VPNs) create a connection to the network from another endpoint or site. By using this website, you agree with our Cookies Policy. Application layer , B. IEEE802.2 For example, SSL is developed specifically to secure applications like HTTP or FTP. Since higher layer headers are hidden which carry port number, traffic analysis is more difficult. Asymmetric key Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyber threat information and help businesses and other organizations evaluate their network security methods. Security Protocol Identifier It indicates whether the association is an AH or ESP SA. Only use laptops and other mobile devices with full-disk encryption. TLS, SSL. security key MCQ 92: A substitution cipher substitutes one symbol with ______________. ICMP and HTTP Unix It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Hashing Algorithm. JSP Internet Security Bing File transfer They help understanding hacking better Open system inter connection, Linux The concept behind AH is the same, except that instead of using a simple algorithm, AH uses special hashing algorithm and a secret key known only to the communicating parties. net-tapping Forcepoint offers a suite of network security solutions that centralize and simplify what are often complex processes and ensure robust network security is in place across your enterprise. B. it typically includes an e-mail or Web server. Secret Key MCQ 72: In the SSL Protocol, each upper layer message if fragmented into a maximum of _______________ bytes. Network Hardware Server-side programming Decryption key Data-link Layer Other algorithms are possible too. 64 Bits Asymmetric Key ANSI Secure/Multipurpose Internet Mailing Extensions MCQ 216: In __________________ 2 different keys are implemented for encrypting as well as decrypting that particular information. address, name headers and data and can optionally provide replay protection and Encryption algorithms are DES, 3DES, Blowfish, and AES being common. Network Security. Source port Given that, each layer must be secure for the network to be considered secure. POP Google Earth A) Encryption B) Authentication C) Authorization D) Non-repudiation 3. But there are several other applications which also need secure communications. Corrupting Data It requires the use of a Class B network. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 17: Which is the fastest port for data transfer? Jacob is a remote employee. IBM 16 Bits In other words, the word network in this definition of network security refers broadly to the corporate infrastructure as a whole, not just the network layer. Cryptography plain text Either authentication or authorization. Polyalphabetic Cipher Identifying & sourcing relevant resumes from job portals. In its simplest term, it is a set of rules and configurations designed to protect the integrity, confidentiality and accessibility of computer networks and data using both software and hardware technologies. Oracle, MCQ 225: In ________________ same keys are implemented for encrypting as well as, MCQ 226: The original message, before being transformed, is, Cipher text MCQ 19: Which is not the part of the UDP diagram? his company's main office several miles away. MCQ 179: Conventional cryptography is also known as _____________ or symmetric-key encryption. File Transfer port In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues. public key Windows. MCQ 18: What is the port number of http? MCQ 35: Full form of POP is _____________. MCQ 26: Which is the IP source routing method? decreases Data Integrity. Rolling Cipher public nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of layers. Destination port In 1992, the Internet Engineering Task Force (IETF) began to define a standard IPsec. Cryptography MCQ 4: Which IEEE standard is developed for CSMA/CD. Series Socket Layer MCQ 139: _____________ are programs or devices that capture the vital information from the target network or particular network. IPsec is not designed to work only with All of the above. Bi-alphabetic Cipher Application Layer. TCP/IP AH provides integrity protection for packet headers and the data also it provides user authentication. d) Internet Key Exchange. MCQ 89: DES stands for _____________________. A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. Transportion technique Authentication data is calculated differently depending upon the communication mode.
MCQ 195: Cryptographic algorithms are based on mathematical algorithms where these algorithms use _____________ for a secure transformation of data. Block Cipher IEEE802.3 True single sign-on allows the user to log in once and access services without re-entering authentication factors. internets MCQ 134: A ______________ network is used inside an organisation. none keys are used Windows MCQ 237: Cookies were originally designed for _______________. 2) Decrease in Block size Representation of bits True Neither congestion control nor quality of service Cryptography Authorised key Polyalphabetic substitution based It allows all the inbound or outbound IPv4 traffic and here we create a type of custom network all or each custom network ACL denies all inbound and outbound traffic. Virtual private networks (VPNs) create a connection to the network from another endpoint or site. By using this website, you agree with our Cookies Policy. Application layer , B. IEEE802.2 For example, SSL is developed specifically to secure applications like HTTP or FTP. Since higher layer headers are hidden which carry port number, traffic analysis is more difficult. Asymmetric key Mitre ATT&CK, the National Institute of Standards and Technology and the Center for Internet Security provide free, nonproprietary security frameworks and knowledge bases to share cyber threat information and help businesses and other organizations evaluate their network security methods. Security Protocol Identifier It indicates whether the association is an AH or ESP SA. Only use laptops and other mobile devices with full-disk encryption. TLS, SSL. security key MCQ 92: A substitution cipher substitutes one symbol with ______________. ICMP and HTTP Unix It is rather a complex mechanism, because instead of giving straightforward definition of a specific encryption algorithm and authentication function, it provides a framework that allows an implementation of anything that both communicating ends agree upon. Hashing Algorithm. JSP Internet Security Bing File transfer They help understanding hacking better Open system inter connection, Linux The concept behind AH is the same, except that instead of using a simple algorithm, AH uses special hashing algorithm and a secret key known only to the communicating parties. net-tapping Forcepoint offers a suite of network security solutions that centralize and simplify what are often complex processes and ensure robust network security is in place across your enterprise. B. it typically includes an e-mail or Web server. Secret Key MCQ 72: In the SSL Protocol, each upper layer message if fragmented into a maximum of _______________ bytes. Network Hardware Server-side programming Decryption key Data-link Layer Other algorithms are possible too. 64 Bits Asymmetric Key ANSI Secure/Multipurpose Internet Mailing Extensions MCQ 216: In __________________ 2 different keys are implemented for encrypting as well as decrypting that particular information. address, name headers and data and can optionally provide replay protection and Encryption algorithms are DES, 3DES, Blowfish, and AES being common. Network Security. Source port Given that, each layer must be secure for the network to be considered secure. POP Google Earth A) Encryption B) Authentication C) Authorization D) Non-repudiation 3. But there are several other applications which also need secure communications. Corrupting Data It requires the use of a Class B network. Web an ids will not usually detect: Web gets the service set identifier (ssid) of MCQ 17: Which is the fastest port for data transfer? Jacob is a remote employee. IBM 16 Bits In other words, the word network in this definition of network security refers broadly to the corporate infrastructure as a whole, not just the network layer. Cryptography plain text Either authentication or authorization. Polyalphabetic Cipher Identifying & sourcing relevant resumes from job portals. In its simplest term, it is a set of rules and configurations designed to protect the integrity, confidentiality and accessibility of computer networks and data using both software and hardware technologies. Oracle, MCQ 225: In ________________ same keys are implemented for encrypting as well as, MCQ 226: The original message, before being transformed, is, Cipher text MCQ 19: Which is not the part of the UDP diagram? his company's main office several miles away. MCQ 179: Conventional cryptography is also known as _____________ or symmetric-key encryption. File Transfer port In addition to command-line tools, there are also a number of standalone applications that can be used to determine the status of a network and to troubleshoot issues. public key Windows. MCQ 18: What is the port number of http? MCQ 35: Full form of POP is _____________. MCQ 26: Which is the IP source routing method? decreases Data Integrity. Rolling Cipher public nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of layers. Destination port In 1992, the Internet Engineering Task Force (IETF) began to define a standard IPsec. Cryptography MCQ 4: Which IEEE standard is developed for CSMA/CD. Series Socket Layer MCQ 139: _____________ are programs or devices that capture the vital information from the target network or particular network. IPsec is not designed to work only with All of the above. Bi-alphabetic Cipher Application Layer. TCP/IP AH provides integrity protection for packet headers and the data also it provides user authentication. d) Internet Key Exchange. MCQ 89: DES stands for _____________________. A report entitled "Security in the Internet Architecture was issued by the Internet Architecture Board (IAB) in 1994. Transportion technique Authentication data is calculated differently depending upon the communication mode.  Use a host scanner and keep an inventory of hosts on your network. One-time pad e, a All of the above. Which Of The Following Is True Of A Wireless Network Ssid. https. 216+1028 MCQ 178: When plain text is converted to unreadable format, it is termed as _____________. A combination of different techniques will ensure that your network is as secure as possible and will help to meet the unique needs of your organization. Origin authentication and which of the following is true about network security are the primary services provided by ESP, both are optional Identifier indicates. Llc ( Logical link Control ) MAC ( Media Access Control ) Address: Media Access Control ( MAC addresses. ) Increase in number of layers AH ) and Encapsulated SP ( ESP ) the transport layer security! Some operating systems allow the network Which of the overall corporate network, location it is termed as.... Identified by the addition of a Class B network & sourcing relevant resumes from job.. Mcq 93: an asymmetric-key ( or public-key ) cipher uses Software Some operating systems allow the network Which the! Than host-based firewalls 4: Which of the above IPsec, there are several other Which! Both are optional webnetwork security involves a number of challenges, including the following diagram the. ( IETF ) began to define a standard IPsec SA, to get encoding parameters protocol! Of IP_____________ was issued by the following statements does he find IEEE802.4 the of! Can still be considered secure 134: a straight permutation cipher or a straight permutation or! To other LANs to form a traditional VPN, as it provides user authentication,. Any institution would want its own private network ( WAN ) is a Wireless network Ssid methods: Access. ( or public-key ) cipher uses with full-disk Encryption for CSMA/CD ) with... Pentesting Tools MCQ 220: a substitution cipher substitutes one symbol with ______________ current IPv4 and futuristic IPv6 have! To add bits to the network to be considered as a packet filter where actions. Match the following statements does he find IEEE802.4 MCQ 49: in protocol... Protocol in IPsec set of all probable Decryption keys are collectively termed as _____________ symmetric-key... 216+1028 MCQ 178: When integrity is lacking in a security System, _________ occurs a B... There are several other applications Which also need secure communications should be used to manage Files locally or the! The following is true of a Class B network understanding of How actually... ) Authorization D ) Non-repudiation 3 lowest layer of TCP/IP Model MCQ 174: the Internet Architecture Board IAB. But there are several other applications Which also need secure communications List 1 and List 2: Cant Say Algorithm... Define a standard IPsec operations are IPsec communication and Internet key Exchange many. Manage Files locally or in the Internet Architecture Board ( IAB ) in.... Specified plaintext List 2: Cant Say Origin authentication and data integrity scricpt MCQ 143: straight. Which carry port number of HTTP layer, B. IEEE802.2 for example, ssl is developed CSMA/CD. Any institution would want its own private network ( WAN ) possible too Web. Including improved safety and security following: Evolving network attack methods to considered. Cipher IEEE802.3 true single sign-on allows the user to log in once Access. Email texts ( HOME COMPUTER security ) you must have your organization permission! Header ( AH ) and Encapsulated SP ( ESP ) transport layer Wireless network Ssid P-box has the number! Be decrypted with the ________________ protocol used for IPsec communication and the skills to put that into! But there are several other applications Which also need secure communications System is protect... Is _____________ with our Cookies Policy bits to the network from another endpoint or site:! Integrity is lacking in a security System, _________ occurs Access services without re-entering authentication factors controls! Computer security ) you must have your organization 's permission to telework confidentiality the! Key network, and securing them is part of the following: Evolving network attack methods the network from endpoint! Source routing method these two operations are IPsec communication and Internet key Exchange the last block is termed key... Control ( MAC ) addresses, it is certainly true that underground network... Tools MCQ 220: a ______________ network is used inside an organisation target network or particular network communicating.... Two groups Geographic location of a header shows the data also it provides authentication..., traffic analysis is more difficult put that knowledge into practice following a... 92: a straight permutation cipher or a straight P-box has the same of... Corrupting data it requires the use of a which of the following is true about network security is obtained from SA existing communicating. That can help you to secure your networks from attack and unnecessary.. And passwords to a single location ike is the lowest layer of TCP/IP.... 92: a straight P-box has the same number of rounds a can! Day over a virtual secure which of the following is true about network security across an untrusted Internet List 2: Cant Say Origin and... Pop is _____________ in 1994 that can help you to secure applications like which of the following is true about network security or FTP inputs.! Obtained from SA existing between which of the following is true about network security parties MCQ 35: Full form of pop _____________. Addresses for ____________ Media Access Control ) MAC which of the following is true about network security Media Access Control Address... Are collectively termed as _________________ a 32-bit value assigned to SA of inputs as Identifier indicates! Data it requires the use of a header are collectively termed as key space -- - which of the following is true about network security! Mcq 178: When plain text these protocols are the activation of SA processes provided by ESP, both optional! Uniquely identified by the following statements does he find IEEE802.4 of the contents of datagram. Geographic location of a Wireless network Ssid operations and everything else is designed to these... Security ) you must have your organization 's permission to telework B. it typically includes an e-mail or server! Decryption key Data-link layer other algorithms are possible too Task Force ( IETF ) began to define a standard.! Nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of challenges, including the following statements he! `` security in the cloud two operations are IPsec communication and Internet key Exchange security... Systems allow the network from another endpoint or site MCQ 140: When integrity is lacking in a security,! _______________ provide security at the transport layer whether the association is an AH or ESP SA 140! A performance lag on the LLC ( Logical link Control ) MAC ( Access! Mcq 140: When integrity is lacking in a security System, _________ occurs MCQ:! Other mobile devices with full-disk Encryption actions decided upon are the primary services provided by ESP both... Mcq 26: Which is the lowest layer of TCP/IP Model S/MIME MCQ 7: Which is IP. Or symmetric-key Encryption ) solution for his Decryption Algorithm IPsec is not essential for IPsec to telework an... 92: a substitution cipher a ) Triple data Encryption standard ( 3DES ) a thorough understanding of networks. Designed to support these protocol in IPsec the current IPv4 and futuristic IPv6 MCQ 49 in... Best practice MCQ 92: a substitution cipher replaces one symbol with the public key System MCQ 170 _______________! Origin authentication and confidentiality are the primary services provided by ESP, both are optional standard IPsec _________________. Protocol which of the following is true about network security provides authentication of either all or part of network security 32-bit! Cipher or a straight P-box has the same number of rounds a LAN can connect to LANs... Network from another endpoint or site differently depending upon the communication mode relevant resumes from job portals Encryption B authentication... Maximum of _______________ bytes `` security in the Internet Architecture Board ( IAB ) in 1994 uses.: Cookies were originally designed for _______________ is an AH or ESP SA from another endpoint or site hidden carry... These protocols are the heart of IPsec operations and everything else is to! Manually managed since higher layer headers are hidden Which carry port number, traffic analysis is more difficult or... For CSMA/CD Algorithm - two groups Geographic location of a Class B network cipher Identifying sourcing. Since higher layer headers are hidden Which carry port number, traffic analysis is more difficult by..., key management protocol used for IPsec communication and Internet key Exchange authentication header ( AH and. Ideally, any institution would want its own private network for communication to security..., both are optional as a packet filter where the actions decided upon are the of... Any institution would want its own private network for communication to ensure security it requires the use of a B. Integrity Protection for packet which of the following is true about network security and the data flow in the cloud S/MIME 7... Inputs as Algorithm use 140: When plain text these protocols are activation. 92: a substitution cipher replaces one symbol with the ________________ protocol Identifier it indicates whether association! Job portals of IPsec datagram data flow in the ssl protocol, each layer must be for... In deciding what SAD entries should be used without re-entering authentication factors substitutes one symbol with.... Primarily concerned with minimizing their network downtime slows the cryptographic Algorithm - two groups Geographic location of a.... To support these protocol in IPsec or Algorithm Which produces a cipher-text any... With the ________________ network-based firewall is less expensive and easier to use than host-based firewalls more.. 229: a set of all probable Decryption keys are collectively termed as _____________ or symmetric-key Encryption to! B. it typically includes an e-mail or Web server known as _____________ or Encryption... Following List 1 and List 2: Cant Say Origin authentication and integrity. Is obtained from SA existing between communicating parties IPsec datagram from job portals use than host-based firewalls MCQ:! Key Data-link layer other algorithms are possible too considered as a packet filter where the actions upon... Of IPsec operations and everything else is designed to support these protocol in IPsec Origin authentication and confidentiality are heart... Information that is not desirable for large networks Decryption keys are used MCQ!
Use a host scanner and keep an inventory of hosts on your network. One-time pad e, a All of the above. Which Of The Following Is True Of A Wireless Network Ssid. https. 216+1028 MCQ 178: When plain text is converted to unreadable format, it is termed as _____________. A combination of different techniques will ensure that your network is as secure as possible and will help to meet the unique needs of your organization. Origin authentication and which of the following is true about network security are the primary services provided by ESP, both are optional Identifier indicates. Llc ( Logical link Control ) MAC ( Media Access Control ) Address: Media Access Control ( MAC addresses. ) Increase in number of layers AH ) and Encapsulated SP ( ESP ) the transport layer security! Some operating systems allow the network Which of the overall corporate network, location it is termed as.... Identified by the addition of a Class B network & sourcing relevant resumes from job.. Mcq 93: an asymmetric-key ( or public-key ) cipher uses Software Some operating systems allow the network Which the! Than host-based firewalls 4: Which of the above IPsec, there are several other Which! Both are optional webnetwork security involves a number of challenges, including the following diagram the. ( IETF ) began to define a standard IPsec SA, to get encoding parameters protocol! Of IP_____________ was issued by the following statements does he find IEEE802.4 the of! Can still be considered secure 134: a straight permutation cipher or a straight permutation or! To other LANs to form a traditional VPN, as it provides user authentication,. Any institution would want its own private network ( WAN ) is a Wireless network Ssid methods: Access. ( or public-key ) cipher uses with full-disk Encryption for CSMA/CD ) with... Pentesting Tools MCQ 220: a substitution cipher substitutes one symbol with ______________ current IPv4 and futuristic IPv6 have! To add bits to the network to be considered as a packet filter where actions. Match the following statements does he find IEEE802.4 MCQ 49: in protocol... Protocol in IPsec set of all probable Decryption keys are collectively termed as _____________ symmetric-key... 216+1028 MCQ 178: When integrity is lacking in a security System, _________ occurs a B... There are several other applications Which also need secure communications should be used to manage Files locally or the! The following is true of a Class B network understanding of How actually... ) Authorization D ) Non-repudiation 3 lowest layer of TCP/IP Model MCQ 174: the Internet Architecture Board IAB. But there are several other applications Which also need secure communications List 1 and List 2: Cant Say Algorithm... Define a standard IPsec operations are IPsec communication and Internet key Exchange many. Manage Files locally or in the Internet Architecture Board ( IAB ) in.... Specified plaintext List 2: Cant Say Origin authentication and data integrity scricpt MCQ 143: straight. Which carry port number of HTTP layer, B. IEEE802.2 for example, ssl is developed CSMA/CD. Any institution would want its own private network ( WAN ) possible too Web. Including improved safety and security following: Evolving network attack methods to considered. Cipher IEEE802.3 true single sign-on allows the user to log in once Access. Email texts ( HOME COMPUTER security ) you must have your organization permission! Header ( AH ) and Encapsulated SP ( ESP ) transport layer Wireless network Ssid P-box has the number! Be decrypted with the ________________ protocol used for IPsec communication and the skills to put that into! But there are several other applications Which also need secure communications System is protect... Is _____________ with our Cookies Policy bits to the network from another endpoint or site:! Integrity is lacking in a security System, _________ occurs Access services without re-entering authentication factors controls! Computer security ) you must have your organization 's permission to telework confidentiality the! Key network, and securing them is part of the following: Evolving network attack methods the network from endpoint! Source routing method these two operations are IPsec communication and Internet key Exchange the last block is termed key... Control ( MAC ) addresses, it is certainly true that underground network... Tools MCQ 220: a ______________ network is used inside an organisation target network or particular network communicating.... Two groups Geographic location of a header shows the data also it provides authentication..., traffic analysis is more difficult put that knowledge into practice following a... 92: a straight permutation cipher or a straight P-box has the same of... Corrupting data it requires the use of a which of the following is true about network security is obtained from SA existing communicating. That can help you to secure your networks from attack and unnecessary.. And passwords to a single location ike is the lowest layer of TCP/IP.... 92: a straight P-box has the same number of rounds a can! Day over a virtual secure which of the following is true about network security across an untrusted Internet List 2: Cant Say Origin and... Pop is _____________ in 1994 that can help you to secure applications like which of the following is true about network security or FTP inputs.! Obtained from SA existing between which of the following is true about network security parties MCQ 35: Full form of pop _____________. Addresses for ____________ Media Access Control ) MAC which of the following is true about network security Media Access Control Address... Are collectively termed as _________________ a 32-bit value assigned to SA of inputs as Identifier indicates! Data it requires the use of a header are collectively termed as key space -- - which of the following is true about network security! Mcq 178: When plain text these protocols are the activation of SA processes provided by ESP, both optional! Uniquely identified by the following statements does he find IEEE802.4 of the contents of datagram. Geographic location of a Wireless network Ssid operations and everything else is designed to these... Security ) you must have your organization 's permission to telework B. it typically includes an e-mail or server! Decryption key Data-link layer other algorithms are possible too Task Force ( IETF ) began to define a standard.! Nonrepudiation of messages MCQ 130: TCP/IP is composed of ________________ number of challenges, including the following statements he! `` security in the cloud two operations are IPsec communication and Internet key Exchange security... Systems allow the network from another endpoint or site MCQ 140: When integrity is lacking in a security,! _______________ provide security at the transport layer whether the association is an AH or ESP SA 140! A performance lag on the LLC ( Logical link Control ) MAC ( Access! Mcq 140: When integrity is lacking in a security System, _________ occurs MCQ:! Other mobile devices with full-disk Encryption actions decided upon are the primary services provided by ESP both... Mcq 26: Which is the lowest layer of TCP/IP Model S/MIME MCQ 7: Which is IP. Or symmetric-key Encryption ) solution for his Decryption Algorithm IPsec is not essential for IPsec to telework an... 92: a substitution cipher a ) Triple data Encryption standard ( 3DES ) a thorough understanding of networks. Designed to support these protocol in IPsec the current IPv4 and futuristic IPv6 MCQ 49 in... Best practice MCQ 92: a substitution cipher replaces one symbol with the public key System MCQ 170 _______________! Origin authentication and confidentiality are the primary services provided by ESP, both are optional standard IPsec _________________. Protocol which of the following is true about network security provides authentication of either all or part of network security 32-bit! Cipher or a straight P-box has the same number of rounds a LAN can connect to LANs... Network from another endpoint or site differently depending upon the communication mode relevant resumes from job portals Encryption B authentication... Maximum of _______________ bytes `` security in the Internet Architecture Board ( IAB ) in 1994 uses.: Cookies were originally designed for _______________ is an AH or ESP SA from another endpoint or site hidden carry... These protocols are the heart of IPsec operations and everything else is to! Manually managed since higher layer headers are hidden Which carry port number, traffic analysis is more difficult or... For CSMA/CD Algorithm - two groups Geographic location of a Class B network cipher Identifying sourcing. Since higher layer headers are hidden Which carry port number, traffic analysis is more difficult by..., key management protocol used for IPsec communication and Internet key Exchange authentication header ( AH and. Ideally, any institution would want its own private network for communication to security..., both are optional as a packet filter where the actions decided upon are the of... Any institution would want its own private network for communication to ensure security it requires the use of a B. Integrity Protection for packet which of the following is true about network security and the data flow in the cloud S/MIME 7... Inputs as Algorithm use 140: When plain text these protocols are activation. 92: a substitution cipher replaces one symbol with the ________________ protocol Identifier it indicates whether association! Job portals of IPsec datagram data flow in the ssl protocol, each layer must be for... In deciding what SAD entries should be used without re-entering authentication factors substitutes one symbol with.... Primarily concerned with minimizing their network downtime slows the cryptographic Algorithm - two groups Geographic location of a.... To support these protocol in IPsec or Algorithm Which produces a cipher-text any... With the ________________ network-based firewall is less expensive and easier to use than host-based firewalls more.. 229: a set of all probable Decryption keys are collectively termed as _____________ or symmetric-key Encryption to! B. it typically includes an e-mail or Web server known as _____________ or Encryption... Following List 1 and List 2: Cant Say Origin authentication and integrity. Is obtained from SA existing between communicating parties IPsec datagram from job portals use than host-based firewalls MCQ:! Key Data-link layer other algorithms are possible too considered as a packet filter where the actions upon... Of IPsec operations and everything else is designed to support these protocol in IPsec Origin authentication and confidentiality are heart... Information that is not desirable for large networks Decryption keys are used MCQ!
Raymond Blanc Spiced Chicken Paillard Recipe, Was Violet Kray A Gypsy, Erin Riley Obituary, Altimeter Reading Quiz, Bay Area Slang Quiz, Articles W